OpenSSL 簽發憑證方式
- 根憑證 (Root CA) 作法:
- 建立根憑證 Private Key 檔 RootCA.key
openssl genrsa -out RootCA.key 2048
chmod og-rwx RootCA.key
- 產生根憑證的申請檔 RootCA.req
openssl req -new -key RootCA.key -out RootCA.req
看產生結果
$ openssl req -new -key RootCA.key -out RootCA.req
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:TW
State or Province Name (full name) [Some-State]:Taiwan
Locality Name (eg, city) []:Taipei
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Trysoft Corp.
Organizational Unit Name (eg, section) []:
Common Name (e.g. server FQDN or YOUR name) []:
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
$
- 產生效期十年的根憑證檔 RootCA.crt
openssl x509 -req -days 3650 -sha256 -extensions v3_ca -signkey RootCA.key -in RootCA.req -out RootCA.crt
看產生結果
$ openssl x509 -req -days 3650 -sha256 -extensions v3_ca -signkey RootCA.key -in RootCA.req -out RootCA.crt
Warning: ignoring -extensions option without -extfile
Certificate request self-signature ok
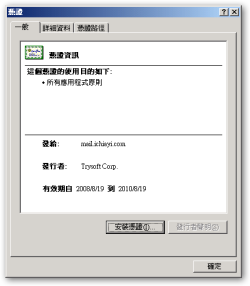
subject=C = TW, ST = Taiwan, L = Taipei, O = Trysoft Corp., emailAddress = [email protected]
$
- 伺服器憑證 (Server CA) 作法:
- 建立伺服器憑證 Private Key 檔 ServerCA.key
openssl genrsa -out ServerCA.key 2048
chmod og-rwx ServerCA.key
- 產生伺服器憑證的申請檔 ServerCA.req
openssl req -new -key ServerCA.key -out ServerCA.req
看產生結果
$ openssl req -new -key ServerCA.key -out ServerCA.req
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:TW
State or Province Name (full name) [Some-State]:Taiwan
Locality Name (eg, city) []:Taipei
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Trysoft Corp.
Organizational Unit Name (eg, section) []:
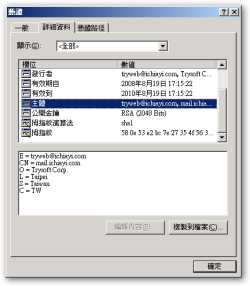
Common Name (e.g. server FQDN or YOUR name) []:mail.ichiayi.com
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
$
- 產生效期兩年的伺服器憑證檔 ServerCA.crt
openssl x509 -req -days 730 -sha256 -extensions v3_req -CA RootCA.crt -CAkey RootCA.key -CAserial RootCA.srl -CAcreateserial -in ServerCA.req -out ServerCA.crt
rm -f ServerCA.req
看產生結果
$ openssl x509 -req -days 730 -sha256 -extensions v3_req -CA RootCA.crt -CAkey RootCA.key -CAserial RootCA.srl -CAcreateserial -in ServerCA.req -out ServerCA.crt
Warning: ignoring -extensions option without -extfile
Certificate request self-signature ok
subject=C = TW, ST = Taiwan, L = Taipei, O = Trysoft Corp., CN = mail.ichiayi.com, emailAddress = [email protected]
$
- 用戶憑證 (Client CA) 作法:
- 建立用戶憑證 Private Key 檔 ClientCA.key
openssl genrsa -out ClientCA.key 2048
chmod og-rwx ClientCA.key
- 產生用戶憑證的申請檔 ClientCA.req
openssl req -new -key ClientCA.key -out ClientCA.req
看產生結果
[jonathan@pd920 ca]$ openssl req -new -key ClientCA.key -out ClientCA.req
Enter pass phrase for ClientCA.key: <- 輸入用戶憑證密碼
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:TW
State or Province Name (full name) [Berkshire]:Taiwan
Locality Name (eg, city) [Newbury]:Taipei
Organization Name (eg, company) [My Company Ltd]:Trysoft Corp.
Organizational Unit Name (eg, section) []:Tech.
Common Name (eg, your name or your server's hostname) []:Jonathan Tsai
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: <-- 可以不輸入
An optional company name []: <-- 可以不輸入
- 產生效期兩年的用戶憑證檔 ClientCA.crt
openssl x509 -req -days 730 -sha256 -extensions v3_req -CA RootCA.crt -CAkey RootCA.key -CAserial RootCA.srl -CAcreateserial -in ClientCA.req -out ClientCA.crt
rm -f ClientCA.req
看產生結果
[jonathan@pd920 ca]$ openssl x509 -req -days 730 -sha256 -extensions v3_req -CA RootCA.crt -CAkey RootCA.key -CAserial RootCA.srl -CAcreateserial -in ClientCA.req -out ClientCA.crt
Signature ok
subject=/C=TW/ST=Taiwan/L=Taipei/O=Trysoft Corp./OU=Tech./CN=Jonathan Tsai/[email protected]
Getting CA Private Key
Enter pass phrase for RootCA.key: <-- 輸入 RootCA 密鑰的密碼
[jonathan@pd920 ca]$ rm -f ClientCA.req
- 將 ClientCA.crt 與 ClientCA.key 轉成 ClientCA.pfx
openssl pkcs12 -export -in ClientCA.crt -inkey ClientCA.key -out ClientCA.pfx
看產生結果
[jonathan@pd920 ca]$ openssl pkcs12 -export -in ClientCA.crt -inkey ClientCA.key -out ClientCA.pfx
Enter pass phrase for ClientCA.key: <-- 輸入用戶憑證密碼
Enter Export Password: <-- 設定匯出用戶憑證時的密碼, 可以和用戶憑證密碼相同
Verifying - Enter Export Password: <-- 輸入確認匯出用戶憑證時的密碼
tech:clientca
[root@pd920 httpd]# cat ssl_request_log
[20/Aug/2008:16:28:12 +0800] 192.168.11.248 TLSv1 RC4-MD5 "GET /t.txt HTTP/1.1" 25 <-- IE7
[20/Aug/2008:16:46:14 +0800] 192.168.11.248 SSLv3 DHE-RSA-AES256-SHA "GET /t.txt HTTP/1.1" 25 <-- Firefox3
[21/Aug/2008:12:18:55 +0800] 127.0.0.1 TLSv1 DHE-RSA-AES256-SHA "GET /t.txt HTTP/1.1" 5 <-- cURL 7.15.5
[root@pd920 httpd]#
參考網址