申請設定 Let's Encrypt 免費 SSL 憑證(CentOS + Apache/Nginx)
因為 Google Chrome 自 2018/05/01 對於沒有合法的 SSL 網站憑證, 就會出現警告, 所以就出現要買 SSL 網站憑證的議題, 針對個人網站或是非正式的公司網站, 採用 Let's Encrypt 免費網站 SSL 憑證似乎是個不錯的選擇.
申請 Let's Encrypt 與設定 Web Server 程序
- Ubunut 20.04
- Alpine 3.16
- CentOS 8
- CentOS 7
載入中 ...
- 這過程會檢查與安裝 python packages 並讀取 web server 的設定, 查看目前的網站網址, 如果有設定 Virtual Host 多網址, 也可以選擇產生多網域的憑證1)
- 原則上只要最後詢問 Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. 是否要讓瀏覽 http 網址自動轉至 https 的問題後, 出現以下的訊息, 就表示已自動將 web server 的設定都改好
: Congratulations! You have successfully enabled https://www.ichiayi.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=www.ichiayi.com :
- 如果只要產生網站憑證檔案, 可以再 certbot 後面加上 certonly 的參數 Exp.
certbot-auto --nginx certonly
- 這樣執行後, 會在 /etc/letsencrypt/live 目錄內, 產生該網域的憑證相關檔案目錄
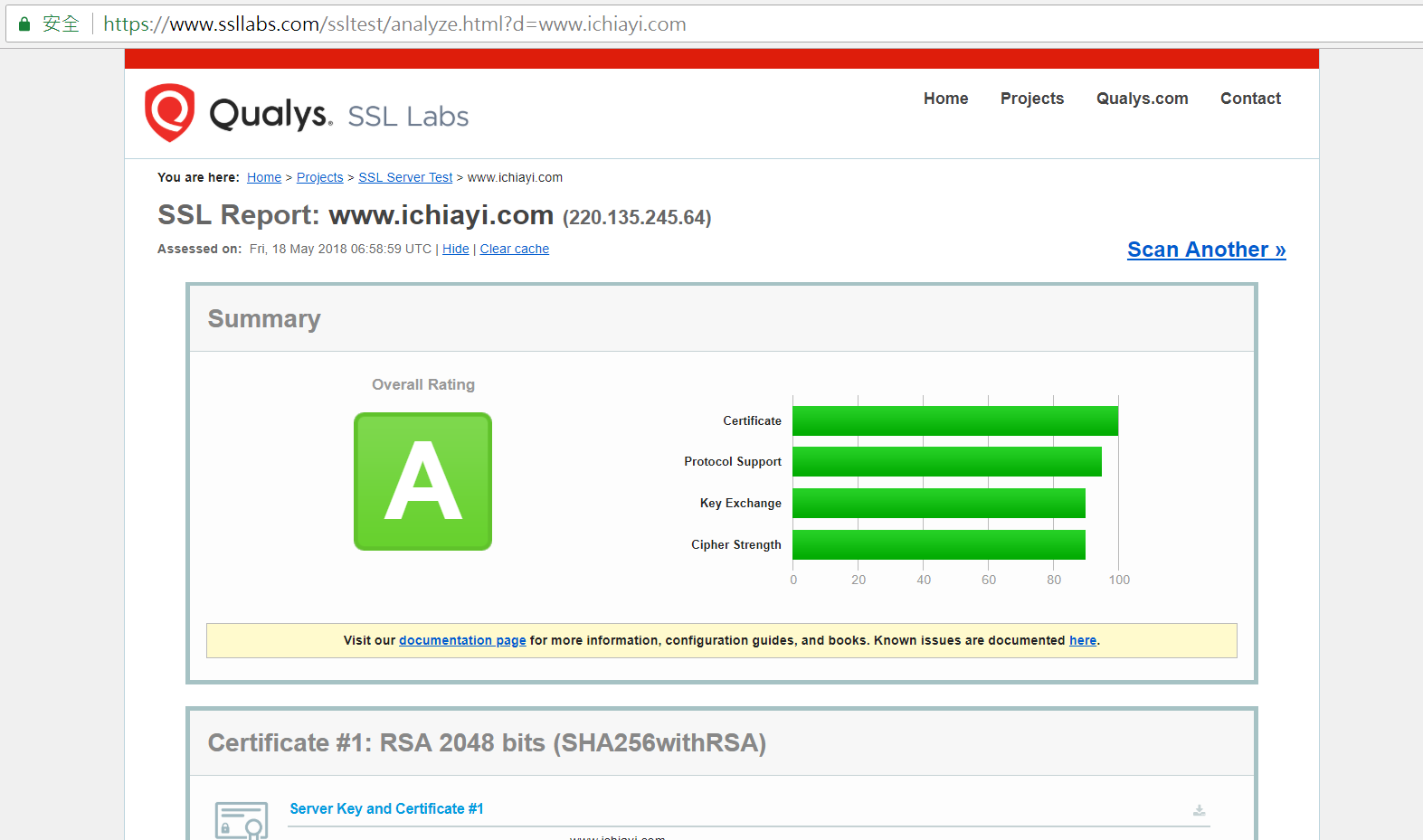
透過 ssllabs 來檢測是否正常
- 其中檢測 CAA Record 這一項需要在 DNS 設定, 如果想完整設定可使用以下網站協助產生設定資料
https://sslmate.com/caa/
當 DNS 完成設定後, 可以使用以下網站功能檢測
https://caatest.co.uk/
apache 相關設定
- 必須要將 /etc/httpd/conf.d/ssl.conf 內的 “SSL Virtual Host Context” 底下預設 VirtualHost 整個拿掉才能正常運作
: ## ## SSL Virtual Host Context ## #<VirtualHost _default_:443> #: #: #</VirtualHost>
- certbot-auto 會自動產生 /etc/httpd/conf/httpd-le-ssl.conf 定義 VirtualHost, 如果沒有產生要直接修改 ssl.conf 點這裡看 wiki.ichiayi.com 範例 點這裡看範例|
: : <VirtualHost *:80> ServerName www.ichiayi.com ServerAdmin [email protected] DocumentRoot /var/www/www.ichiayi.com_html CustomLog logs/www.ichiayi.com-access_log common ErrorLog logs/www.ichiayi.com-error_log Redirect permanent / https://www.ichiayi.com/ </VirtualHost> :
server { server_name www.ichiayi.com; access_log /var/log/nginx/www.ichiayi.com.access.log main; error_log /var/log/nginx/www.ichiayi.com.error.log; location / { : : } listen 443 ssl; # managed by Certbot ssl_certificate /etc/letsencrypt/live/www.ichiayi.com/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/www.ichiayi.com/privkey.pem; # managed by Certbot include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot } server { if ($host = www.ichiayi.com) { return 301 https://$host$request_uri; } # managed by Certbot listen 80; server_name www.ichiayi.com; return 404; # managed by Certbot }
設定自動更新憑證
- 因為免費憑證只有 3 個月的有效期, 所以自動檢查與更新是很重要
- certbot 就具有自動更新的功能, 可設定每天檢查三次(00:00 08:00 16:00), 執行時先隨機取 3600 中的一個秒數等待, 避免造成同時間大家一起連上 Let's Encrypt 主機, 方式如下
- CentOS 7
vi /etc/crontab
: # let's encrypt 0 */8 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && certbot renew > /tmp/cert-bot_renew.log
service crond restart
- 之後就可以在 /tmp/cert-bot_renew.log 看到檢查更新的紀錄
手動申請 *.ichiayi.com 的 SSL 網域憑證方式
- 執行以下的語法
/root/lets-encrypt/certbot-auto -d ichiayi.com -d *.ichiayi.com --manual --preferred-challenges dns certonly --server https://acme-v02.api.letsencrypt.org/directory
- 當出現以下第二次的 Before continuing, verify the record is deployed. 必須去設定 ichiayi.com 的 DNS
Please deploy a DNS TXT record under the name _acme-challenge.ichiayi.com with the following value: 0sGmQQTfit9lW3okOa4jaYmefNQS4FsF6zZgEtyppKw Before continuing, verify the record is deployed. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Press Enter to Continue - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please deploy a DNS TXT record under the name _acme-challenge.ichiayi.com with the following value: fEsd-DYrN-AB_XVWb-Aa9Yx9OxCofBlFkxNmt7RWiCk Before continuing, verify the record is deployed.
- 將前面兩次出現的 hash 值正確設定到 ichiayi.com 的 DNS TXT Record 內, Exp.
: ; $TTL 86400 ; 1 day -- ; 3 hours $ORIGIN ichiayi.com. @ IN SOA ns1 server ( 2018123100 ; serial 28800 ; refresh (2 hours) 14400 ; retry (15 minutes) 720000 ; expire (1 week) 86400 ; minimum (12 hours) ) NS ns4.everplast.net. NS ns7.ichiayi.com. ; ; lets-encrypt SSL Cert _acme-challenge IN TXT "0sGmQQTfit9lW3okOa4jaYmefNQS4FsF6zZgEtyppKw" _acme-challenge IN TXT "fEsd-DYrN-AB_XVWb-Aa9Yx9OxCofBlFkxNmt7RWiCk" ; : - 重新啟動 DNS 讓這兩個 TXT 生效, 可透過 nslookup 指定詢問 server 8.8.8.8 來確認
C:\Users\jonathan>nslookup 預設伺服器: UnKnown Address: 192.168.1.5 > server 8.8.8.8 預設伺服器: google-public-dns-a.google.com Address: 8.8.8.8 > _acme-challenge.ichiayi.com 伺服器: google-public-dns-a.google.com Address: 8.8.8.8 名稱: _acme-challenge.ichiayi.com > set type=txt > _acme-challenge.ichiayi.com 伺服器: google-public-dns-a.google.com Address: 8.8.8.8 未經授權的回答: _acme-challenge.ichiayi.com text = "fEsd-DYrN-AB_XVWb-Aa9Yx9OxCofBlFkxNmt7RWiCk" _acme-challenge.ichiayi.com text = "0sGmQQTfit9lW3okOa4jaYmefNQS4FsF6zZgEtyppKw" - 確認可以正確查詢到這兩個新增的 TXT Record 後才可執行下一步, 當出現以下訊息就表示正確產生
: Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/ichiayi.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/ichiayi.com/privkey.pem Your cert will expire on 2019-03-31. To obtain a new or tweaked version of this certificate in the future, simply run certbot-auto again. To non-interactively renew *all* of your certificates, run "certbot-auto renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
相關重點檔案
- /root/lets-encrypt/certbot-auto (下載時指定位置)
- /etc/letsencrypt/ 存放執行 certbot-auto 自動申請 SSL 相關憑證與檔案
- /var/log/letsencrypt/ 存放執行 certbot-auto 的紀錄檔案
透過 CloudFlare DNS 自動更新無 Web 對外網站 SSL 憑證
- 因為部份網站是內部網站, 並無法對外透過 Web 方式認證自動更新憑證, 所以需要透過 DNS 即時建立 TXT Record 來認證, 如要自動認證, 就需要透過 DNS 提供整合 API 才能達成
- Ubuntu 20.04
- CentOS 8
- CentOS 7
- CentOS 6
載入中 ...
Ubuntu 20.04
- 安裝 DNS CloudFlare Plugin
apt install python3-certbot-dns-cloudflare
- 建立 /root/lets-encrypt/cloudflare.ini
mkdir -p /root/lets-encrypt/
Exp:
# Cloudflare API credentials used by Certbot dns_cloudflare_email = [email protected] dns_cloudflare_api_key = 0123456789abcdef0123456789abcdef01234567
- 設定保護權限
chmod 600 /root/lets-encrypt/cloudflare.ini
- 進行申請新憑證 Exp. example.com
/usr/bin/certbot certonly \ --dns-cloudflare \ --dns-cloudflare-credentials /root/lets-encrypt/cloudflare.ini \ --dns-cloudflare-propagation-seconds 10 \ -d example.com
- 進行定期更新憑證 Exp. example.com
/usr/bin/certbot renew \ --dns-cloudflare \ --dns-cloudflare-credentials /root/lets-encrypt/cloudflare.ini \ --dns-cloudflare-propagation-seconds 10
- 設定每天自動檢查更新
- 建立 /root/lets-encrypt/renewcert.sh
vi /root/lets-encrypt/renewcert.sh
/usr/bin/certbot renew \ --dns-cloudflare \ --dns-cloudflare-credentials /root/lets-encrypt/cloudflare.ini \ --dns-cloudflare-propagation-seconds 10
chmod a+x /root/lets-encrypt/renewcert.sh
- 設定 /etc/crontab
vi /etc/crontab
: # let's encrypt 35 2 * * * root /root/lets-encrypt/renewcert.sh > /tmp/renewcert.log
systemctl restart crond
參考網址
1)
只產生一個憑證檔案, 但該憑證檔案內有包含多個網址